Trendaavat aiheet
#
Bonk Eco continues to show strength amid $USELESS rally
#
Pump.fun to raise $1B token sale, traders speculating on airdrop
#
Boop.Fun leading the way with a new launchpad on Solana.
Welcome back to Sherlock's Vulnerability Spotlight, where we highlight an impactful vulnerability uncovered during a Sherlock audit.
This week, we have a Chain Denial of Service (CDoS).
It was uncovered by @0xPapaPitufo during the @MorphLayer L2 contest.
🧵👇

In Rollup.sol, if a malicious batch is proposed, the assumption is that the sequencer who proposed it will lose the challenge, get slashed, and the chain will be reset. These economic incentives prevent the chain from being regularly halted.
This is based on the assumption that a sequencer can only win challenges if the batch they proposed is valid.
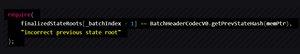
However, the check that prevStateRoot is the postStateRoot of the previous batch only happens in finalizeBatch(). This check is sufficient to prevent batches with fake prevStateRoots from being finalized, but it does not stop these batches from being committed.
This allows a malicious sequencer to propose any batch that performs a valid state transaction on a fake prevStateRoot.
In most cases, a challenger will attack this invalid batch. However, the sequencer can provide a valid proof of this state transition to steal the honest challenger's deposit and win the challenge.
In the case that this happens, or that no challenge is performed, the committed batch will not be able to be finalized due to the following check:
This will freeze the chain and not allow any new batches to be finalized, since batches are committed sequentially and must be finalized sequentially.
The Attack Path:
1) Attacker proposes a batch that contains a valid state transition from a fake prevStateRoot.
2) If an honest challenger challenges the batch, the attacker provides a valid proof of the state transition to win the challenge and steal the challenger's deposit.
3) Whether or not the above happens, the chain is now halted, as the attacker's batch cannot be finalized, and no other batches can be finalized without it being finalized first.
4) The attacker will not be slashed, because they won the challenge.
What's the impact?
An honest challenge that will lose its deposit when a dishonest sequencer beats it in a challenge, and no new batches will be able to be finalized, causing Denial of Service of the Chain, and will have to be manually rolled back by the admins.
The Mitigation:
Check in commitBatch() that prevStateRoot is equal to the parentBatchHeader.postStateRoot.
We are proud to have helped secure @morphlayer through this discovery.
When it absolutely needs to be secure, Sherlock is the right choice.
3,08K
Johtavat
Rankkaus
Suosikit













