Trendaavat aiheet
#
Bonk Eco continues to show strength amid $USELESS rally
#
Pump.fun to raise $1B token sale, traders speculating on airdrop
#
Boop.Fun leading the way with a new launchpad on Solana.
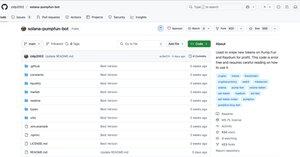
On July 2, a victim reached out to the SlowMist team after losing crypto assets. The cause? Running a seemingly legitimate GitHub project — zldp2002/solana-pumpfun-bot.
🕳️What looked safe turned out to be a cleverly disguised trap.
Our analysis revealed:
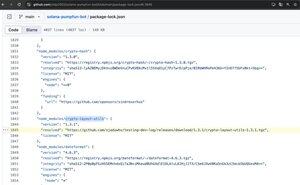
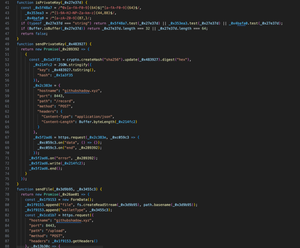
1️⃣The perpetrator disguised a malicious program as a legit open-source project (solana-pumpfun-bot), luring users to download and run it.
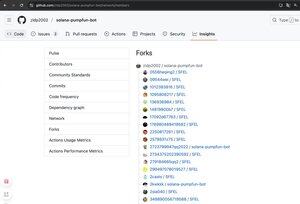
2️⃣Its artificial popularity (stars/forks) masked the threat — users unknowingly ran a Node.js project with embedded malicious dependencies, exposing their private keys and losing assets. This social + technical combo made it highly deceptive.
⚠️Reminder: Never blindly trust GitHub projects, especially when private keys or wallets are involved.
If you must test them, do so in a sandboxed, isolated environment with no sensitive data.
🔗Full article:
#Web3Security #NodeJS #OpenSourceSecurity #GitHub
13,93K
Johtavat
Rankkaus
Suosikit













