Trendaavat aiheet
#
Bonk Eco continues to show strength amid $USELESS rally
#
Pump.fun to raise $1B token sale, traders speculating on airdrop
#
Boop.Fun leading the way with a new launchpad on Solana.
Post-quantum cryptography is entering deployment.
ICICLE by @Ingo_zk now supports ML-KEM (Kyber) with full param sets, batching, and async ops.
Let's unpack this one! 👇
@Ingo_zk ML-KEM (Module-Lattice Key Encapsulation Mechanism) is the standardised Kyber variant under FIPS 203, designed for post-quantum cryptography.
NIST approved three levels: Kyber512 (Level 1), Kyber768 (Level 3), and Kyber1024 (Level 5).
@Ingo_zk ICICLE v3.9.0 implements ML-KEM in C++ with full support for all three parameter sets. Key operations—key generation, encapsulation, decapsulation—are template-instantiated via Kyber{512,768,1024}Params.
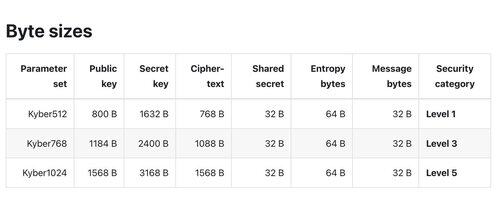
@Ingo_zk Byte sizes per param set:
- Kyber512: PK=800B, SK=1632B, CT=768B
- Kyber768: PK=1184B, SK=2400B, CT=1088B
- Kyber1024: PK=1568B, SK=3168B, CT=1568B
@Ingo_zk The MlKemConfig struct supports async ops, device residency hints (e.g. public_keys_on_device), and batching (batch_size). Tuning hooks via ConfigExtension* ext are available for backend-specific optimisation.
@Ingo_zk API signatures:
- keygen(entropy, config, public_keys, secret_keys)
- encapsulate(message, public_keys, config, ciphertexts, shared_secrets)
- decapsulate(secret_keys, ciphertexts, config, shared_secrets)
@Ingo_zk Batching enables parallelism in key exchange—critical for scalable applications like secure messaging and PQ VPNs. Device-side flags hint to ICICLE runtime about pre-existing memory locations to minimize transfers.
@Ingo_zk ICICLE includes example usage for Kyber768: allocation, entropy gen, keypair generation, encapsulation, and decapsulation. The pattern is structured and consistent across parameter sets.
@Ingo_zk This implementation aligns with the NIST FIPS 203 final spec (June 2025). It's tailored for integration in PQC-aware C++ applications, especially those leveraging hardware acceleration.
1,88K
Johtavat
Rankkaus
Suosikit













