Trendaavat aiheet
#
Bonk Eco continues to show strength amid $USELESS rally
#
Pump.fun to raise $1B token sale, traders speculating on airdrop
#
Boop.Fun leading the way with a new launchpad on Solana.

Phylax Systems
App-defined security enforced by networks
"'Trust us, we're secure" isn't good enough anymore.
Your users have heard this before. From protocols that got drained. From platforms that promised safety. From auditors who missed critical flaws.
Smart users don't trust. They verify.
With Phylax, they can.
Every security assertion protecting their funds is public. Every invariant is written in readable code. Every protection can be independently verified by anyone with basic Solidity knowledge (or even without soon).
No black box algorithms. No proprietary security models. No 'trust our process.'
Just transparent proofs that anyone can read and verify.

211
"'Trust us, we're secure" isn't good enough anymore.
Your users have heard this before. From protocols that got drained. From platforms that promised safety. From auditors who missed critical flaws.
Smart users don't trust. They verify.
With Phylax, they can.
Every security assertion protecting their funds is public. Every invariant is written in readable code. Every protection can be independently verified by anyone with basic Solidity knowledge (or even without soon).
No black box algorithms. No proprietary security models. No 'trust our process.'
Just transparent, mathematical proofs that anyone can read and verify.

199
Phylax Systems kirjasi uudelleen
tbh this is exactly why we're building phylax
robinhood doesn't want to use a general-purpose chain because they can't control the security model.
they need guarantees that their users won't get rekt by some defi exploit or bridge hack that they had nothing to do with
779
Another great breakdown by our devrel.

jacob Φ10.7. klo 23.31
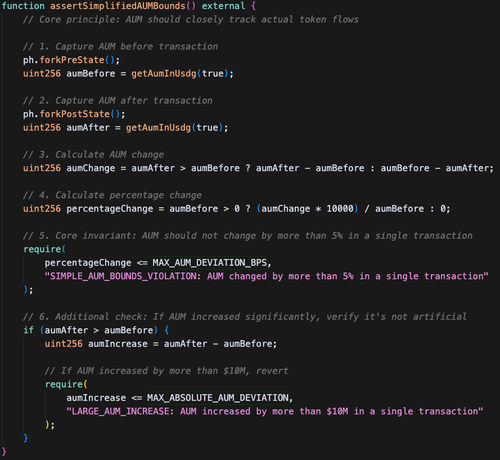
GMX v1 Lost $42M Through AUM Manipulation
Yesterday GMX v1 suffered an attack that drained $42M through AUM manipulation. This was GMX's 2nd major hack of 2025 (lost $13M in March).
Disclaimer: This is not a full post-mortem, I've mainly looked into the AUM manipulation part.
The Attack Vector:
1. Exploited reentrancy in `executeDecreaseOrder` function
2. During callback, opened massive short positions at artificially low prices
3. Manipulated `globalShortAveragePrices`, inflating AUM calculation
4. System thought it had huge "unrealized profits" from shorts
5. Redeemed GLP tokens at inflated prices, extracting real assets
The Core Issue:
GMX's AUM = Physical Tokens + Stablecoins + Unrealized Trading Profits + Fees
When shorts lose money (current price > average price), the vault "profits" and AUM increases. The attacker exploited this to create artificial profits.
Simple Prevention:
An AUM bounds invariant enforcing `AUM_change ≤ net_token_inflow + 5%` would have caught this immediately.
The attack created massive artificial value with minimal real deposits - exactly what economic sanity checks detect.
A simplified version of a @phylaxsystems assertion that could have detected and prevented the hack:
764
Johtavat
Rankkaus
Suosikit
Ketjussa trendaava
Trendaa X:ssä
Viimeisimmät suosituimmat rahoitukset
Merkittävin


















