Trendaavat aiheet
#
Bonk Eco continues to show strength amid $USELESS rally
#
Pump.fun to raise $1B token sale, traders speculating on airdrop
#
Boop.Fun leading the way with a new launchpad on Solana.
Be careful that your assets are running naked
Not your keys, not your coins😶
The old people in the currency circle often say that "if you don't have your own private key, then these assets don't really belong to you", and security is even more on this basis.
The incident of "Douyin bought a cold wallet of 50 million yuan was stolen overnight" once again reminds everyone that safety is the most important part on the road to prosperity.
Today, Rabbit Sangui will introduce the "source pass" and "use pass" of the wallet, and discuss how to protect the security of our wallet.
1⃣ Be sure to close the source before buying
1. Never buy from unofficial channels, only from the official website or from the official list of authorized dealers.
For example, the so-called "brand new, unopened" or "special price flash sale" hardware wallets in many unauthorized third-party e-commerce channels are likely to be cracked and implanted in the backdoor of the device, and must not be touched!
2. Check the integrity of the sealing film and tamper-evident seal when receiving, and reject it decisively if it is found to be abnormal.
Don't use equipment with incomplete packaging if you don't want to return it for a momentary convenience.
At the same time, even if the packaging is intact, it may be that it has been repackaged during transportation, and some high-imitation devices have similar appearances, but the internal chips and random number generators cannot guarantee safety or have a back door.
So be sure to follow the official verification process to check the authenticity of your wallet!
Before, a group of friends came up with a cold wallet for Rabbit Sangui, and Rabbit Sangui directly refused, and he must be responsible for his own assets and refuse the second-hand wallet.
3. When you first boot up, let the wallet run off the network, and be sure to generate a mnemonic phrase in an offline environment.
At the same time, please use paper or metal plates to record the mnemonic phrase, and do not take photos, screenshots, cloud backups, etc.
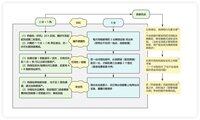
The emphasis on "the build phase must be offline" is because 👇
The private key/mnemonic phrase is the only chance to be "visible & tamperable" at this moment. Although it is possible to plug in the USB in the future, it is very difficult for an attacker to read or affect the private key.
After that, if you want to do bad things with USB in the later stages, you will encounter a lot of resistance 👇
✅ Hardware ACL protection
(1) Want the device to spit out the private key? Instructions do not exist and do not spit out
(2) Want to secretly read internal Flash? The address is not on the whitelist and cannot be read
✅ Firmware signature protection
(1) If a hacker wants to flash a new firmware with a backdoor, they must spoof the vendor's private key (mathematically impossible).
Forging signatures requires an exhaustive 2 to the 256th power of the key or cracking a discrete logarithm (both of which are beyond the power of modern and predictable computing)
(2) Any unsigned code pushed by BadUSB (malicious) will be rejected by the bootloader.
The bootloader is the earliest line of defense for our device to boot, and it is burned into read-only or write-protected Flash, which cannot be overwritten by the back-flashed firmware (the bootloader verifies the firmware signature with the manufacturer's public key).
✅ PIN lock protection (with self-destruct/delay policy)
(1) Even if the attacker gets the physical object, he needs to guess the PIN correctly before he can invoke the signature command.
(2) Brute-force attacks will be delayed or directly erased, which is equivalent to "private key burning".
In addition to being sure to control the "source" before purchasing, you should also pay attention to safety during use.
2⃣ Precautions for daily use
1. Prevent man-in-the-middle attacks from address tampering.
For example, when transferring money, check the address information one by one on the device screen, and do not try to compare only the last few digits to prevent the clipboard from being tampered with.
2. Connect to a secure device (e.g. upgrade ROM, sign, etc.) for daily use, and disconnect immediately after completion.
3. Hot wallets only hold small amounts of funds, and large amounts are stored in cold wallets, and do not concentrate all funds on one device.
It is also what we often say: don't put your eggs in one basket~
4. Verify the mnemonic phrase regularly to confirm that the backup is available.
5. Large assets can use 2-of-3 hardware multi-signature
Similar to wanting to open a door, you need to use any 2 of the 3 keys, which not only improves the ability to resist attacks, but also retains a certain amount of redundancy.
(For example, 2 cold wallets + 1 hot wallet, assuming that the cold wallet is A, B, and the hot wallet is C)
Such benefits are as follows 👇
(1) If hot wallet C is compromised by hackers, cold wallet A + cold wallet B can still prevent the funds from being transferred.
(2) In case cold wallet A is broken, as long as cold wallet B + hot wallet C are still there, you can get back the assets.
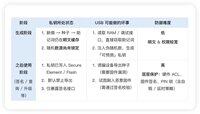
Some friends may ask, what about my three cold wallets? Here is a brief comparison of the advantages and disadvantages 👇 of "2 cold, 1 hot" and "3 cold".
6. Cold wallets and mnemonic phrases are stored in different locations (multi-location disaster recovery, avoiding one-pot ends)
#加密安全 #硬件钱包
Finally, as the cliché goes, if you don't have your own private keys, then these assets don't really belong to you, and safe use is built on this foundation!
If you have other experience, please leave a message to add it 🥰
I just received a cold wallet from KeyStone's official, and my sister said that purple is very charming~
Thanks to Brother Sea for the group @Sea_Bitcoin, and to Brother Bill @bc1Bill and Keystone @KeystoneWallet for the official gifts 🥰
Thank you again for your African refugee physique, grab the smallest red envelope, lose the east, and receive the mulberry 🤪

3,67K
Johtavat
Rankkaus
Suosikit













